Category: Security

Speculative Execution Vulnerabilities – Meltdown & Spectre
On Jan 3, 2018, Google’s Project Zero team along with several other university researchers identified several security issues with speculative execution, an optimization technique used in microprocessors to improve performance. Couchbase is aware of the recently disclosed class of processor/OS...
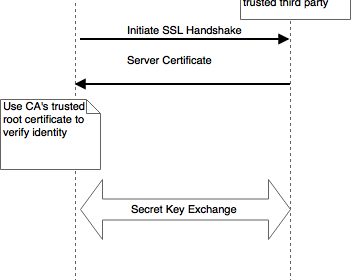
Certificate Pinning in Android with Couchbase Mobile
Couchbase Mobile 2.0 supports certificate pinning on all Couchbase mobile platforms. Certificate pinning is a technique used by applications to “pin” a host to it’s certificate/public key. Communication between Couchbase Lite and Sync Gateway is encryped and secured using SSL/TLS....

Announcing Couchbase Server 5.0
Couchbase Server 5.0 is here!!! I am thrilled to announce the availability of this major release. Couchbase Server 5.0 is the latest release of the most powerful NoSQL technology. Couchbase Server, the foundation of the Couchbase Data Platform, allows enterprises...

CURL Comes to N1QL: Querying External JSON Data
JSON is a helpful way to transmit data. Now, N1QL can query it thanks to a CURL update in Couchbase 5.0. See how to connect to various endpoints to do just that. N1QL has many functions that allow you to...

Putting a Zipper on the Back of the Hospital Gown
Last week, security firm Appthority published a report titled HospitalGown: The Backend Exposure Putting Enterprise Data at Risk, which highlighted newly-discovered vulnerabilities between mobile apps and insecure backend databases containing enterprise data. The vulnerability is caused not by code in...

Authentication and Authorization with RBAC in .NET
Authentication and authorization are vastly improved in Couchbase Server 5.0. We’ve been blogging about the new RBAC features in the developer preview for a while. Authentication and Authorization with RBAC – introduction / part 1 Authentication and Authorization with RBAC...

Improved SDK Authentication Methods – Couchbase 5.0
Couchbase Server 5.0 delivers some great new authentication features that require some minor changes to your client connection code. The specific changes to the SDK are outlined in this post and also refer to changes made in the pre-release April Developer Build as...

Authorization & Authentication with RBAC (Part 2)
Authorization and authentication are important to Couchbase. In March, I blogged about some of the new Role Based Access Control (RBAC) that we are showing in the Couchbase Server 5.0 Developer Builds. This month, I’d like to go into a...

Authentication and Authorization with RBAC
In March’s developer build, you can start to see some major changes to authentication and authorization within Role Based Access Control (RBAC) coming to Couchbase Server. These changes are a work in progress: the developer build is essentially a nightly...

Introducing Role-Based Access Control in Couchbase Server 4.5
Over the years, it has been drilled into me to use “Least Privilege” access whenever and however possible. This specially applies to administrators – they manage important IT infrastructure components like NoSQL databases, and have the liberty to use all...

Introducing Couchbase Server 4.6.0 Developer Preview
Today, we’re very excited to announce the availability of Couchbase Server 4.6.0 DP. This is an early developer release that comes with some exciting capabilities for cross datacenter replication, security, query, tools, and powerful full text search capability. The Developer...

Skipping default bucket creation
Some days ago I made the following search: “databases unprotected”. It is really incredible the number of databases deployed without authentication. Most of them are just test databases published on the internet, but others are exposing sensitive data. (Image Licensed through...