Category: Best Practices and Tutorials
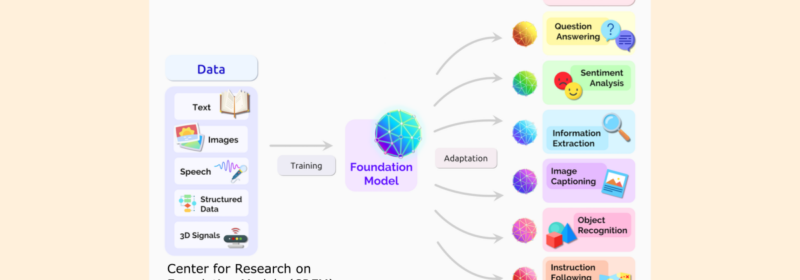
What are Foundation Models? (Plus Types and Use Cases)
What is a Foundation Model? A foundation model is a powerful type of artificial intelligence (AI) trained on massive amounts of general data, allowing it to tackle a broad range of tasks. Foundation models, such as OpenAI’s GPT (Generative Pre-trained...

SAML Integration Simplified: Connecting Microsoft Entra with Couchbase Server for Secure SSO
In today’s digital landscape, businesses are continuously seeking efficient ways to manage their access control and authentication processes. Integrating Microsoft Entra (formerly known as Azure AD) with Couchbase Server offers a robust and secure solution for single sign-on (SSO) using...

Chat With Couchbase Technical Documentation
Couchbase community: Meet the Couchbase Docs chatbot, your new Generative AI-powered documentation assistant. Now available on the docs.couchbase.com website, the new chatbot will transform the way you learn about Couchbase products. It’s like having a Couchbase expert that’s always on...
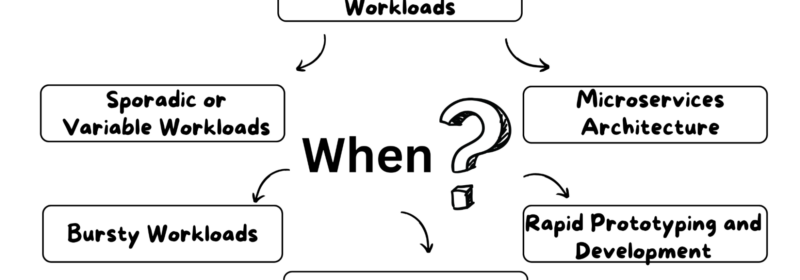
A Guide to Serverless Functions
Serverless functions have become a popular application development and deployment approach. By abstracting infrastructure management and embracing event-driven architecture, they offer a flexible solution for developers. The main goal of serverless is to eliminate the need for infrastructure management and...

Getting Ready for SAML: Essential Preparations for Couchbase Server Integration
In the evolving landscape of digital security, the integration of Couchbase with a Security Assertion Markup Language (SAML) Identity Provider (IdP) stands as a cornerstone for robust authentication mechanisms. Why Should You Implement SSO with Couchbase Server? Single Sign-On (SSO)...

Migrate From MongoDB to Couchbase in Minutes With the CLI and IDE Plugins
Trying Couchbase just got even easier, you can now import your MongoDB data and indexes into Couchbase seamlessly. Whether you prefer working directly from the command line, or within your favorite IDE, our various new offerings—cbmigrate CLI, Couchbase VSCode Extension,...

Improved Debuggability for SQL++ User-Defined Functions
User-defined functions (UDFs) are a very useful feature supported in SQL++. Couchbase 7.6 introduces improvements that allow for more debuggability and visibility into UDF execution. This blog will explore two new features in Couchbase 7.6 in the world of UDFs. Profiling...

Column-Store vs. Row-Store: What’s The Difference?
When’s the last time you used a database? Most of us are so accustomed to user-friendly interfaces like TikTok, bank apps, and work programs that we don’t realize we’re interacting with databases all the time. We’re even less inclined to...
Learning on the Couch with FreeCodeCamp: Version Control – Git + GitHub
If you’d like to watch this blog live, here is a video of Nyah Macklin & Jessica Rose walking through the process of installing Git and setting up a GitHub account. Watch below or read on. In our last post,...

Differences Between Serverless vs. Cloud Computing
Overview of Serverless Computing and Cloud Computing This blog post will discuss the main differences between serverless and cloud computing, their advantages and disadvantages, and their primary use cases. Keep reading to learn which type of computing is the best...
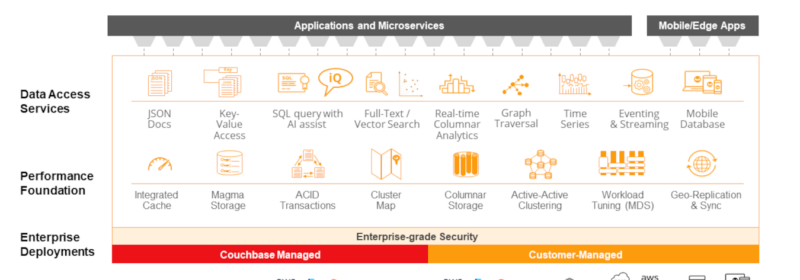
Consolidate Your Databases to Eliminate Data Sprawl, Reduce Complexity and Lower Costs
The concept of consolidation is simple, and applying its principles can bring immense benefit to any organization. But what does consolidation mean in the context of database technology? Google defines consolidation as “the action or process of combining a number of...

What is Vector Similarity Search?
Vector Similarity Search Overview Vector similarity search is a technique that finds similar content or data according to their vector representations. Imagine each piece of data as a collection of numbers arranged in a specific way. By comparing these collections...
